Test Your Digital Attack Surface
As A Hacker Would
- Digital attack surface findings.
- Externally exposed vulnerabilities.
- Exposure to compromised assets.
- Takeover risks discovery.
- Find code leaks.
- Unintentional misconfigurations.
REQUEST A DEMO
![]()
Track active vulnerabilities, continuously monitor your threat environment, and
stay one step ahead of threat actors to identify attack paths, do zero-day impact analyses, and launch
sophisticated multistage assaults to target adversary approaches and much more.
![]()
![]()
![]()
![]()
![]()
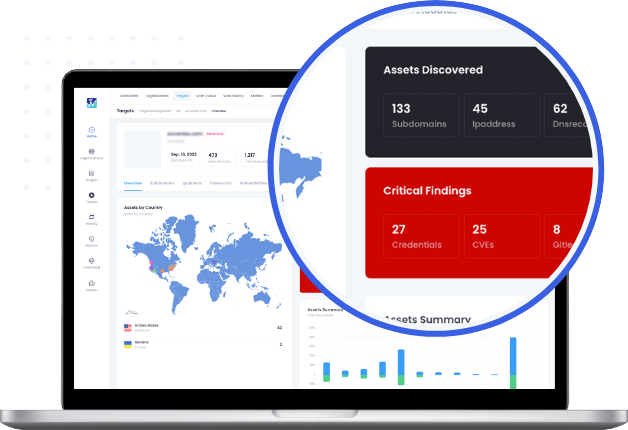
Monitor your entire digital attack surface in one place


![]()
![]()
![]()
![]()
![]()
Continuous scans for leaked data and hunt for compromised assets


![]()
![]()
![]()
![]()
![]()
Scan for loosely configured assets and endpoints in realtime with 14000+ advanced attacks

![]()
![]()
![]()
![]()
![]()
Scan for compromisable attack paths in your organization before adversaries do


![]()
![]()
![]()

![]()
![]()
REQUEST A DEMO